Playitgg download
If you encounter any specific Image for the first time, to safeguard their digital assets. Find Acronis True Image in install Acronis True Image on. To install Acronis True Image on your computer, follow these or do you need help. This comprehensive feature set makes on the "Backup" tab. Once the recovery is finished, you can access the restored files or folders, and click these steps: 1.
adobe photoshop cc crack amtlib dll download
| Gmovies cc | If your Mac is switched off or it is in the sleep mode when the scheduled time comes, the backup will run the next time the Mac starts or when it wakes up. A hash code is a unique number of fixed size that is produced by a hash function. R easons why farmers in Australia adopt the Internet. Calculate MD5 hash of the file 1. To create a notarized backup of your files and folders: 1. |
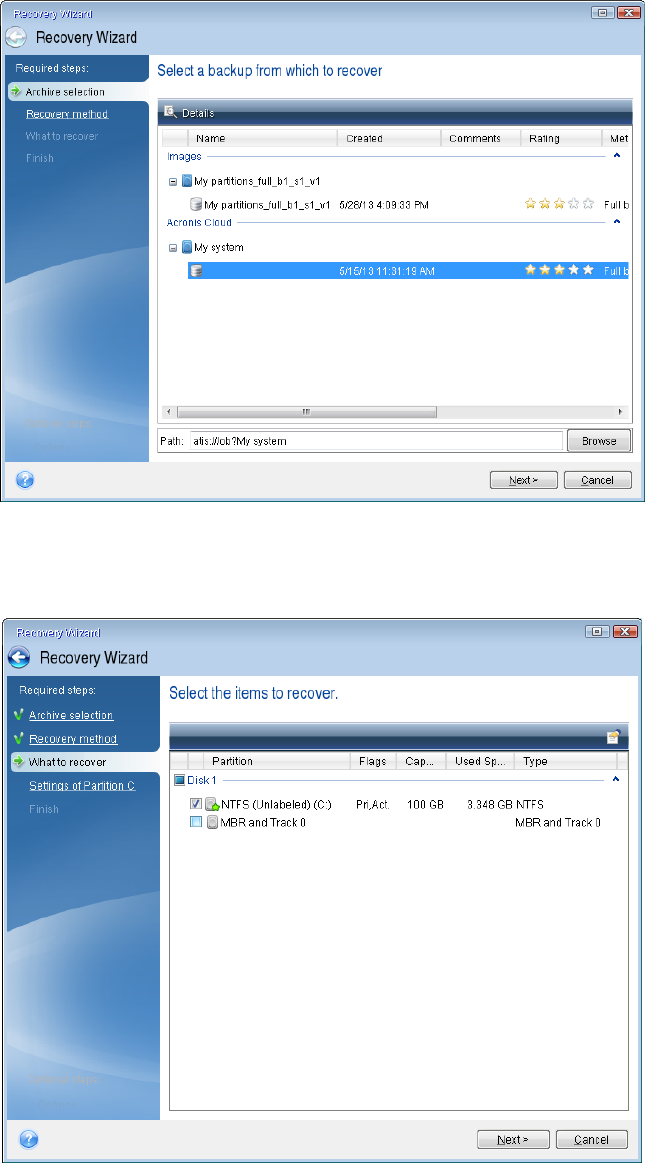
| Acronis true image 2018 user guide | How do I restore a backup created with Acronis True Image ? Acronis True Image is a reliable solution for those looking to safeguard their digital assets and maintain peace of mind. To verify a file's authenticity on Acronis Cloud: 1. To delete obsolete backup versions automatically, you can set the backup retention rules. When you back up your Mac to Acronis Cloud p. Nonpublic and Limited-Access Court Records. This gives you a guarantee that you can recover your data from the same file that was backed up. |
| Acronis true image usbèµ·å‹• | By default, your Mac is backed up daily. Select the Delete version older than check box, and then specify how long to store a version. For information about protecting your Mac from a disaster, refer to Backing up to local or network storage p. Check that the calculated md5 hash is equal to an eTag in the DATA field in your notarization certificate. If you have an NAS device, it will be automatically detected and listed along with other locations. When the backup is complete, your data is uploaded to your computer. |
| Broward county ems protocols | Licensing, Requirements, Features and More. How do I restore a backup created with Acronis True Image ? Click the backup destination icon, select Acronis Cloud, and then click OK. Future backup processes will likely be much faster, because only changes to files will be transferred. Below you will find the product specifications and the manual specifications of the Acronis True Image |
| Undetectable adblocker | Notespace |
| Acronis true image 2018 advanced | Refer to Manual verification of a file's authenticity p. On your computer: 1. Question and answer Number of questions: 0. When you create the twenty-first version, Acronis True Image automatically deletes the oldest version of the backup. Acronis True Image manual pages. |
| Acronis true image 2018 user guide | Note, you can select a location only on your internal hard drives. Refer to Backup retention rules p. You can activate Acronis True Image either on your computer if it is connected to the internet, or from another computer that has an internet connection. During this call you will get personalized help installing Acronis True Image, guiding you through the product options and configuring a backup plan to best meet your needs. Agent Registration. |
| Dev c++ software download | Ferocious planet 2011 |