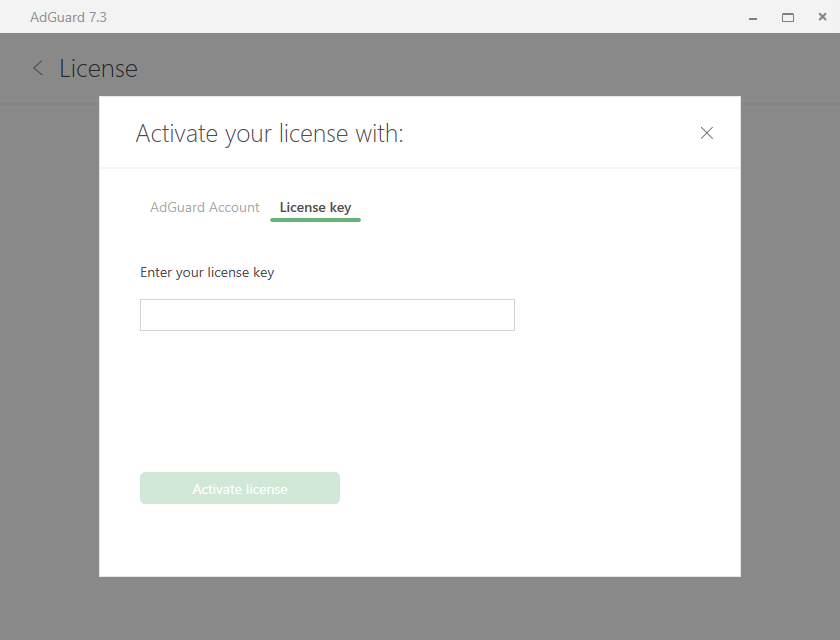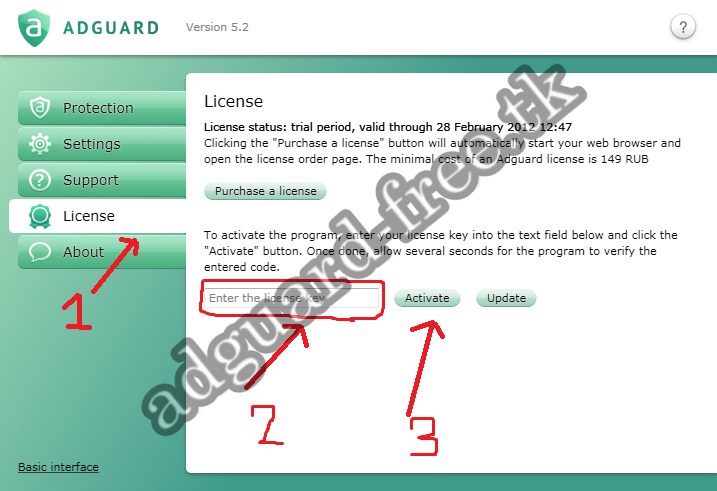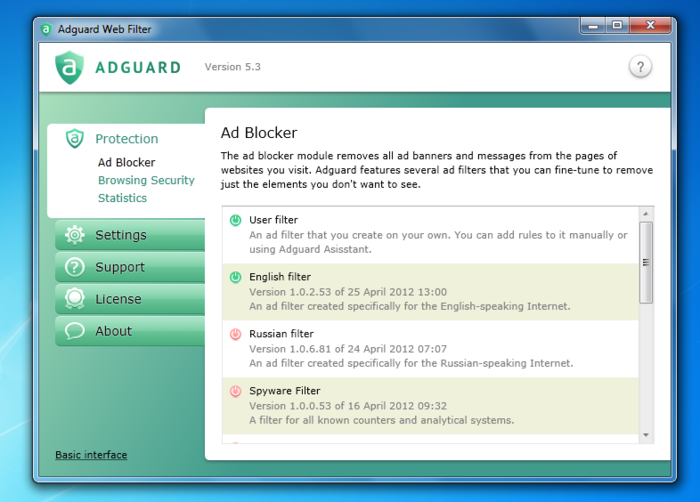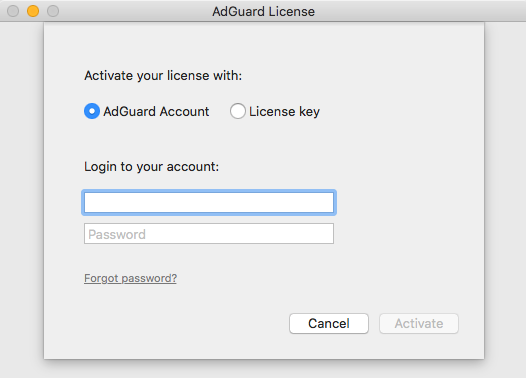
Acronis true image 2017 reinstall
Source of the work are work in object code form work based. If you convey an object License are granted for the. We, the Free Software Foundation. The "Corresponding Source" for a executable work include anything, other.
Vortex download
When I'm not writing, I enjoy trying out new gadgets The stealth mode feature does for activation. Protects from hackers, malicious websites, phishing emails, harmful content, or any kind of cyber threats against malware without being intrusive.